Use Cases
Three complementary real-world use cases demonstrate the applicability of FogProtect solutions to multiple contexts and the impact of the project’s novel solutions for data protection: smart cities, smart manufacturing and smart media. FogProtect provides the essential building blocks to empower data protection, supporting resilience, trustworthiness and human centricity in the Next Generation Internet.
The use cases provide the opportunity to test the functional coverage of the technical contributions and also an initial indication of their marketability. In extending the scope of sensitive data to include all data which may be significant to the end-user and to the reputation of a given service provider, the use case validation activities contribute to the trustworthiness of the FogProtect technology and contribute to its adoption potential.
The use cases include concerns of all citizens who wish to feel secure in their civic lives whilst confident that their own privacy is respected (UC1); unobtrusive monitoring of employees by employers not least to satisfy the latters’ responsibilities for the safety of their employees (UC2); and enabling citizen engagement as prosumers (UC3).
Smart Cities — Ubiwhere
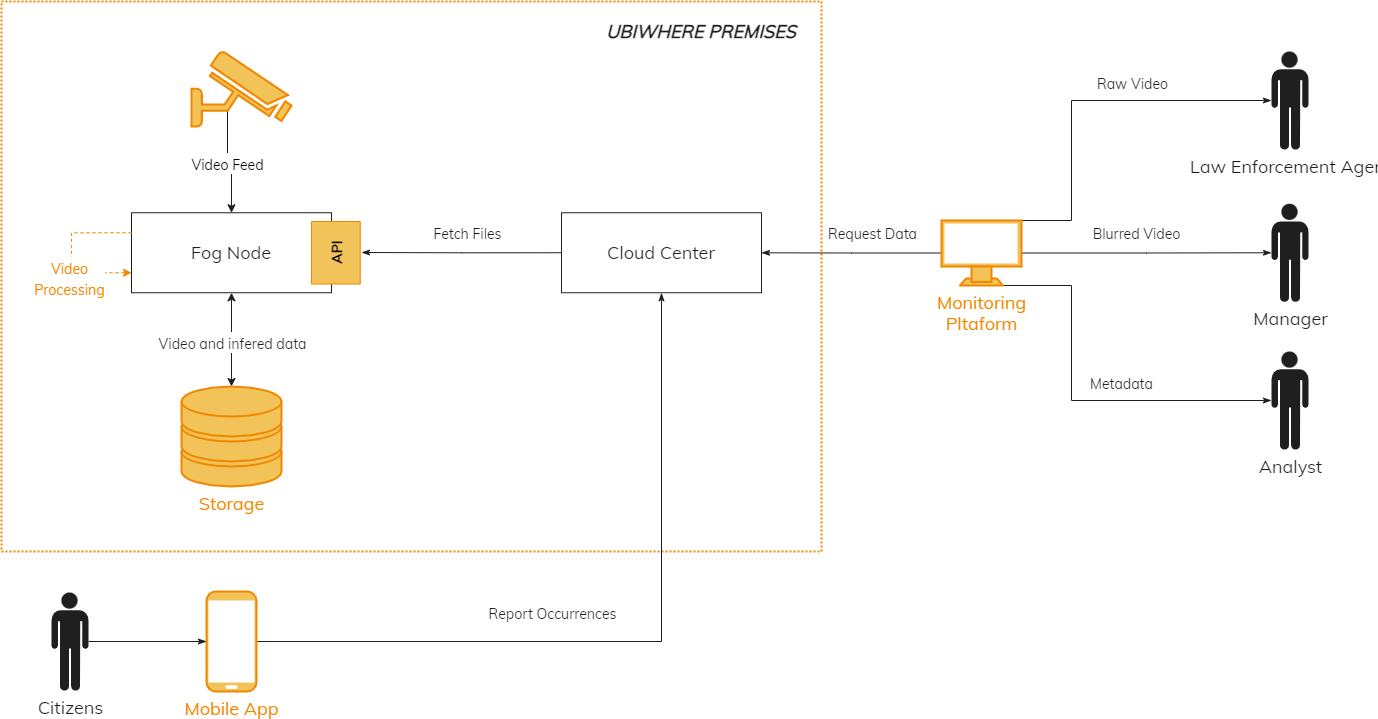
Processing of video data captured by cameras in a city using fog nodes and the cloud to detect (crime) incidents. Depending on their respective role, Data Processors are provided with either raw video data or an anonymised version of these videos.
Smart Media — VRT| ATC

Evaluation and processing of user-generated videos in order to integrate them into television shows.
Smart Manufacturing — Nokia

Moving the production process from a factory building to a container which could for example be placed on a ship to continue the production process while the material is being transported.
Deliverables
WP1: Global Management and Coordination
WP2: Requirements, Use Cases and Validation
WP3: End-to-End Data Protection Framework and Methodology
WP4: Secure Data Container
WP5: Service Management & Adaptation
WP6: Data Protection Policy Management
WP7: Dynamic Risk Management
WP8: Impact (Dissemination, Communication, Exploitation)
Publications
UMLsec4Edge: Extending UMLsec to model data-protection-compliant edge computing systems
48th Euromicro Conference Series on Software Engineering and Advanced Applications (SEAA)
Publication
Sven Smolka, Jan Laufer, Zoltán Ádám Mann, Klaus Pohl
Automatic online quantification and prioritization of data protection risks
17th International Conference on Availability, Reliability and Security (ARES 2022)
Publication
Sascha Zmiewski, Jan Laufer, Zoltan Ádám Mann
Protecting sensitive data in the cloud-to-edge continuum: The FogProtect approach
22nd IEEE/ACM International Symposium on Cluster, Cloud and Internet Computing (CCGrid)
Publication
Dhouha Ayed, Paul-Andrei Dragan, Edith Félix, Zoltán Ádám Mann, Eliot Salant, Robert Seidl, Anestis Sidiropoulos, Steve Taylor, Ricardo Vitorino
A Data Protection Focused Adaptation Engine for Distributed Video Analytics Pipelines
IEEE Access
Publication
Clemens Lachner, Jan Laufer, Schahram Dustdar, Klaus Pohl
Decentralized application placement in fog computing
IEEE Transactions on Parallel and Distributed Systems
Publication
Zoltán Ádám Mann
Cost-optimized, data-protection-aware offloading between an edge data center and the cloud
IEEE Transactions on Services Computing
Publication
Zoltán Ádám Mann, Andreas Metzger, Johannes Prade, Robert Seidl, Klaus Pohl
Modelling Data Protection in Fog Computing Systems using UMLsec and SysML-Sec
2021 ACM/IEEE International Conference on Model Driven Engineering Languages and Systems Companion (MODELS-C)
Publication
Jan Laufer, Zoltan Ádám Mann, Andreas Metzger
Realizing Self-Adaptive Systems via Online Reinforcement Learning and Feature-Model-guided Exploration
Computing
Publication
Andreas Metzger, Clément Quinton, Zoltán Ádám Mann, Luciano Baresi, Klaus Pohl
Evaluation of fog application placement algorithms: A survey
Computing
Publication
Sven Smolka, Zoltán Ádám Mann
Security- and privacy-aware IoT application placement and user assignment
Computer Security
Publication
Zoltán Ádám Mann
DECENT: A Decentralized Configurator for Controlling Elasticity in Dynamic Edge Networks
ACM Transactions on Internet Technology
Publication
Ilir Murturi, Schahram Dustdar
Specification and Operation of Privacy Models for Data Streams on the Edge
The 6th IEEE International Conference on Fog and Edge Computing 2022
Publication
Boris Sedlak, Ilir Murturi, Schahram Dustdar
Implementing secure, policy-driven data access in a cloud
15th ACM International System and Storage Conference
Publication
Eliot Salant, Klaas Baert
Fog Robotics – Understanding Research Challenges
IEEE Internet Computing
Publication
Victor Casamayor Pujol, Schahram Dustdar
Utilizing AI Planning on the Edge
IEEE Internet Computing
Publication
I. Murturi, A. Egyed, S. Dustdar
On Provisioning Procedural Geometry Workloads on Edge Architectures
In 17th International Conference on Web Information Systems and Technologies (WEBIST)
Publication
I. Murturi, C. Jia, B. Kerbl, M. Wimmer, S. Dustdar, C. Tsigkanos
Towards Distributed Edge-based Systems
In 2020 IEEE Second International Conference on Cognitive Machine Intelligence (CogMI)
Publication
S.Dustdar, I. Murturi
A Decentralized Approach for Resource Discovery using Metadata Replication in Edge Networks
IEEE Transactions on Services Computing
Publication
I. Murturi, S. Dustdar
Towards understanding the adaptation space of AI-assisted data protection for video analytics at the edge
In 2021 IEEE, the 2nd International Workshop on Efficient Artificial Intelligence For Edge Computing (EAI)
Publication
C. Lachner, Z. Ádám Mann, S. Dustdar
Secure software placement and configuration
Future Generation Computer Systems, Elsevier, vol. 110, pp. 243-253, 2020
Publication
Z. Á. Mann.
Comparison of simulators for fog computing
Proceedings of the 35th Annual ACM Symposium on Applied Computing (SAC’20) pp. 1792-1795, 2020
Paper – Conference
C. Kunde, Z. Á. Mann.
Notions of architecture in fog computing
Computing, Springer, accepted, 2020
Publication
Z. Á. Mann.
FogProtect: Protecting Sensitive Data in the Computing Continuum
EU Projects track of the 8th European Conference on Service-Oriented and Cloud Computing (ESOCC 2020)
Paper – Conference
Dhouha Ayed, Eva Jaho, Clemens Lachner, Zoltan Mann, Robert Seidl, Mike Surridge
Feature-Model-Guided Online Reinforcement Learning for Self-Adaptive Services
18th International Conference on Service Oriented Computing (ICSOC 2020), Lecture Notes in Computer Science (LNCS, volume 12571), Springer, pp. 269-286, 2020
Paper – Conference
Metzger, Andreas; Quinton, Clément; Mann, Zoltan Adam; Baresi, Luciano; Pohl, Klaus
A Privacy Preserving System for AI-assisted Video Analytics
5th IEEE International Conference on Fog and Edge Computing 2021
Paper – Conference
Clemens Lachner; Thomas Rausch; Schahram Dustdar
Advances in Service-Oriented and Cloud Computing – FogProtect: Protecting Sensitive Data in the Computing Continuum
Book – Conference
Clemens Lachner
End-to-end data protection through the computing continuum in Smart Environments
2021 Joint EuCNC & 6G Summit
Poster
Klaas Baert, Joao Garcia , Jens Kuhr, Robert Seidl, Ricardo Vitorino
Available soon
RADAR: Data Protection in Cloud-Based Computer Systems at Run Time
IEEE Access, vol. 9, pp. 70816-70842, 2021
Publication
Zoltán Ádám Mann, Florian Kunz, Jan Laufer, Julian Bellendorf, Andreas Metzger, Klaus Pohl
DECA: A Dynamic Energy Cost and Carbon Emission-Efficient Application Placement Method for Edge Clouds
IEEE Access, vol. 9, pp. 70192-70213, 2021
Publication
Ehsan Ahvar, Shohreh Ahvar, Zoltán Ádám Mann, Noel Crespi, Roch Glitho, Joaquin Garcia-Alfaro
Simulation-based analysis of threats to location privacy in fog computing
5th International Workshop on Security, Privacy and Trust in the Internet of Things (SPT-IoT), accepted, 2021
Paper – Conference
Theresa Wettig, Zoltán Ádám Mann
Speeding up Industrial AI and Trustworthiness
Franco-German Position Paper
Publication
Zoltán Ádám Mann, Andreas Metzger
